In Singapore’s fast-paced business landscape, companies are increasingly turning to Enterprise Resource Planning (ERP) systems to optimize processes and enhance operational efficiency.
However, the centralization of sensitive business data within these systems makes them attractive targets for cyber threats. Without proper ERP security, companies risk exposing confidential information and compromising their operations. ERP security is important for protecting this valuable data and maintaining uninterrupted business operations.
In this article, we’ll look at what ERP security entails, why it’s important for businesses, and the best ways to protect these systems from evolving cyber threats. We are also going to address common weaknesses and what businesses can do to strengthen their ERP system.
- ERP security protects ERP systems from unauthorized access and cyber threats, ensuring data confidentiality, integrity, and business continuity.
- Key ERP security elements include access control, data encryption, audits, patch management, and compliance to safeguard business data.
- Explore the best practices for ERP security that include implementing Multi-Factor Authentication (MFA), enforcing strong password policies, regularly updating software, and more.
- ScaleOcean ERP offers robust security features like encryption, multi-factor authentication, and continuous monitoring to protect your business data.
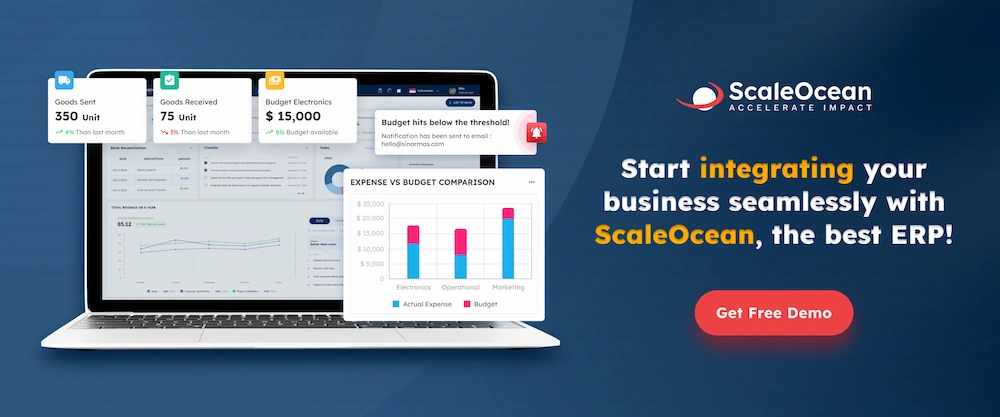
What is ERP Security?
ERP security refers to the practices and technologies used to protect enterprise resource planning (ERP) systems from unauthorized access, data breaches, and cyber threats. ERP security includes putting in place rigorous mechanisms like encryption, access controls, and frequent audits to secure the confidentiality, integrity, and availability of important company data.
By safeguarding ERP systems, businesses can prevent disruptions, maintain compliance with regulations, and protect critical information from cyberattacks. Effective ERP security policies are useful for businesses to reduce risks, improve operational resilience, and maintain stakeholder trust in an increasingly digital landscape.
The Importance of ERP Security
ERP security plays an important role in safeguarding business operations, ensuring compliance, and maintaining trust. It protects sensitive data, ensures adherence to regulations, and prevents disruptions, highlighting the ERP benefits and potential risks of improper security measures. Let’s see why this is important for modern businesses.
1. Data Protection
ERP systems store sensitive information such as financial records, client data, and proprietary company procedures. Robust ERP security guarantees that this data is kept confidential and secure, preventing unwanted access, data breaches, and any misuse that could hurt both the organization and the stakeholders.
2. Regulatory Compliance
Companies must comply with data protection regulations like PDPA. Securing ERP systems prevents fines, penalties, and reputational damage. According to DS Avocats, in the past years, China, India, Indonesia, and Vietnam have updated or introduced data protection laws, emphasizing the need for strong security.
3. Business Continuity
A compromised ERP system can disrupt operations, leading to financial losses and reputational damage. ERP security measures, such as backups and disaster recovery plans, ensure uninterrupted operations, even during cyber incidents, safeguarding productivity and customer trust.
4. Risk Mitigation
Cyber risks such as ransomware and phishing assaults are aimed at ERP systems. Secure ERP implementation eliminates data leakage, lowers the danger of cyberattacks, and protects the company from potential financial and operational losses.
Key Elements of ERP Security

1. Access Control
Implementing role-based access guarantees that users have the necessary permissions, limiting access to sensitive data and functionalities. This reduces the danger of internal breaches and guarantees that only authorized workers can carry out vital duties, hence improving overall system security.
2. Data Encryption
Data encryption protects data at rest and in transit, preventing unauthorized access. The importance of ERP maintenance includes ensuring encryption is up to date, so even if data is intercepted, it remains unreadable, safeguarding confidentiality and maintaining information integrity.
3. Regular Audits
Conducting periodic security assessments helps identify and address vulnerabilities. Audits ensure compliance with security policies, detect suspicious activities, and provide insights for improving the ERP system’s overall security posture.
4. Patch Management
ERP software should be updated and patched on a regular basis to address known vulnerabilities and prevent exploitation. This decreases the risk of cyberattacks while also ensuring the system’s security against evolving threats.
5. Compliance Management
Ensuring that the ERP system complies with industry-specific legislation and standards helps to avoid legal penalties and builds confidence among stakeholders. Compliance displays dedication to data security and ethical business practices.
Best Practices for ERP Security
Implementing best practices for ERP security is vital to protecting sensitive data and ensuring system resilience. The following strategies help businesses mitigate risks, enhance security, and maintain compliance in an evolving digital landscape.
1. Implement Multi-Factor Authentication (MFA)
Adding extra verification steps, like a quick one-time code on top of your password, is a game-changer for security. It’s one of the easiest ways to slash the risk of someone sneaking into your account.
Even if a hacker manages to steal your login info, MFA has your back. It adds a vital second layer of defense that keeps your sensitive business data safe and sound, giving you that extra peace of mind.
2. Enforce Strong Password Policies
Asking for complex passwords and regular updates is a great way to stop brute-force attacks. It’s a simple but effective step to keep hackers out and make sure your system stays locked down tight.
Encouraging the use of password managers helps your team create and store tough passwords safely. This makes things easier for everyone while cutting the risk of anyone getting unauthorized access to your sensitive ERP data.
3. Regularly Update Software
Regularly updating your ERP and apps is the best way to patch up security holes and block cyberattacks. It’s a simple step that keeps your defense strong and your system running smoothly.
Updates do more than just boost security, so they keep your system honest and reliable. By staying current, you protect yourself from threats while ensuring your ERP features are always optimized to handle your growing business needs.
4. Conduct Security Training
Giving your team some cybersecurity awareness training makes it much easier for them to spot threats like phishing or dodgy links. When they know what to look for, they can act as a great first line of defense.
Educated users are a powerful shield against attacks. When your team stays sharp, it really lowers the chances of a simple human mistake turning into a serious security breach or a messy data leak.
5. Monitor System Activity
Setting up tools that watch your system 24/7 lets you track everything as it happens. This real-time view is a game-changer for keeping your business operations running smoothly and staying on top of your security.
Catching odd behavior early lets you react fast to fix security issues. By jumping on threats immediately, you can prevent major disruptions and keep your data safe from the potential harm caused by cyberattacks.
6. Regular Security Audits
Regular security audits are a must to spot any weak points in your ERP. They let you fix risks before they turn into real trouble, keeping you compliant. These checks should look closely at your system setup, who has access, and how safe your data is.
By auditing regularly, you can see if your security is actually working against new cyber threats. This constant review helps you sharpen your protocols, find any gaps, and make the right improvements to keep your ERP system fully protected.
7. Enforced Access Restrictions
Setting up strict access limits is a must for keeping your ERP secure. By making sure only the right people can see or change sensitive data, you protect your system. Using role-based access is a super-effective way to manage these permissions.
Tightening access helps lower the risk of insider threats or unauthorized changes. By giving users only the specific tools they need for their jobs, you keep your data safe and ensure your entire ERP system stays reliable and honest.
8. Data Protection Through Encryption
Data encryption is a must for ERP security, turning sensitive info into unreadable code. It ensures that even if someone sneaks into the system, they can’t make any sense of the data without the right keys, keeping your private details truly private.
By encrypting data while it’s stored or being sent, you add a strong layer of protection. This keeps financial records and customer info safe from cyber-attacks, drastically cutting the risk of data theft or costly breaches for your business.
9. Preparedness with Incident Response Plans
Having an incident response plan is a must for keeping your ERP secure. It’s basically a playbook for what to do if a breach happens, helping you act fast to stop the damage, contain the threat, and get your data back safely.
This plan also sets clear rules for communication so everyone stays in the loop. By regularly testing and updating it, you make sure your team is ready for anything, which really builds up your business’s overall resilience against attacks.
10. Frequent Backups and Recovery Testing
Keeping your ERP safe means backing up your data often and testing your recovery. Regular backups are your best shield against system crashes or cyber-attacks. Testing these steps ensures you can get everything back up and running fast when it counts.
A solid backup plan is key to cutting down downtime if a breach happens. By testing regularly, you’re making sure your data is actually recoverable. It gives you peace of mind that your business can bounce back smoothly after any data loss event.
11. Domain-Specific ERP Testing
Domain-specific ERP testing is all about checking security features built for your specific industry. It makes sure your system is ready for unique security demands, addressing the exact risks and compliance rules your business needs to follow.
This type of testing helps you find vulnerabilities specific to your sector, like retail or manufacturing. It ensures your ERP is set up correctly to handle the unique security hurdles your industry faces, keeping your data much safer.
12. Invest in External Consultancy as Needed
Bringing in outside consultants for ERP security is a smart move to get expert eyes on your system. These specialists spot hidden gaps that internal teams might miss, providing custom advice to keep your sensitive data much safer.
External experts stay on top of the latest threats, which is vital for protecting your ERP. By working with them, your business can strengthen its security and make sure your systems are ready to handle both current and future risks.
ERP and Software Security Challenges
Securing ERP systems is complex due to evolving cyber threats, system integrations, and compliance requirements. Understanding these challenges helps businesses identify vulnerabilities and implement effective security measures to protect their operations and sensitive data.
1. Complexity of ERP Systems
ERP systems are intricate by design, with a variety of interconnected modules that perform different functions. This complexity makes it hard for organizations to easily pinpoint security vulnerabilities, leaving critical weaknesses that could be exploited by attackers.
To address this, businesses need regular security audits and comprehensive monitoring systems. This helps to proactively identify vulnerabilities and implement fixes before they can be exploited, ensuring a more secure and efficient ERP system.
2. Integration with Other Systems
Integrating ERP systems with third-party apps and older systems can open the door to additional risks. If these integrations aren’t managed properly, they could expose the ERP system to external threats, putting the entire network at risk.
The solution is to ensure thorough testing and monitoring of these integrations. Implementing security protocols for all connected systems and regularly reviewing their security posture can help minimize risks and protect the broader ERP ecosystem from breaches.
3. User Access Management
Proper user access management is crucial to protecting sensitive data within an ERP system. By enforcing strong access controls, organizations can restrict data access to only authorized personnel, minimizing the risk of unauthorized data manipulation or breaches.
Inadequate access management can lead to severe data security risks. ERP demos sessions offer businesses a chance to evaluate how user permissions are managed, ensuring that sensitive information remains protected from unauthorized access or misuse by employees or external actors.
4. Compliance and Regulatory Requirements
Every industry has its own set of rules and regulations regarding data handling and privacy. Navigating these regulations while keeping an ERP system secure can be challenging, but failing to comply can lead to severe penalties and loss of trust.
To solve this, companies should ensure their ERP systems are designed with compliance in mind from the start. Regularly updating the system to reflect any changes in regulations and conducting compliance audits can help avoid legal troubles and maintain a trustworthy relationship with customers.
5. Cloud-Based Environments
Cloud-based ERP systems offer great benefits like scalability and flexibility, but they also introduce security risks. Storing sensitive data on the cloud means it’s more susceptible to breaches if not properly secured.
The solution is to use strong encryption, access controls, and frequent security audits for cloud environments. By partnering with cloud providers that follow strict security standards and regularly reviewing the system’s security setup, businesses can keep their data safe from external threats.
6. Phishing and Ransomware Threats
Phishing attacks and ransomware are common threats to ERP systems. A phishing attack tricks users into sharing credentials, while ransomware locks up data and demands a ransom for its release. Both types of attacks can seriously compromise an ERP system’s security.
The solution is to train employees on recognizing phishing attempts and to implement strong email filtering systems. Additionally, having frequent data backups and a robust recovery plan can help businesses quickly recover from ransomware attacks, minimizing downtime and financial loss.
Impact of Unsecured ERP Systems
Failing to secure an ERP system can lead to data breaches, compliance violations, and operational disruptions. Acknowledging these risks enables firms to prevent potential threats and safeguard their systems from costly security vulnerabilities.
1. Operational Disruptions
Security breaches can disrupt a company’s operations, causing downtime and productivity loss. In severe cases, companies may need to suspend operations until the issue is resolved, leading to significant losses, especially for those relying heavily on real-time data and processes
2. Regulatory Fines and Legal Consequences
Companies must comply with data protection regulations, such as the Personal Data Protection Act (PDPA) in Singapore. Non-compliance, particularly following a data breach, can result in hefty fines and legal consequences, including lawsuits from affected customers or business partners.
3. Internal Misuse and External Attacks
ERP systems are often overlooked in cybersecurity, making them vulnerable to internal misuse and external attacks. Regular updates and patches are crucial to protect these systems. According to IBM, with security spending projected to reach USD 377 billion by 2028, safeguarding ERP systems is more important than ever.
Steps to Secure Your ERP Systems
Securing your ERP system requires a proactive approach to protect sensitive data and prevent cyber threats. The following steps help businesses strengthen security, reduce risks, and ensure compliance with industry regulations.
1. Assess Current Security Posture
Evaluate existing security measures, identify vulnerabilities, and analyze potential risks. This step provides a clear understanding of your ERP system’s strengths and weaknesses, forming the foundation for targeted improvements.
2. Develop a Security Strategy
Create a detailed plan that addresses identified vulnerabilities while aligning with business goals. This strategy should include policies, procedures, and technologies to mitigate risks and ensure compliance with industry standards.
3. Implement Security Measures
Implement strong restrictions like encryption, multi-factor authentication, and role-based access management. These methods protect data integrity, restrict illegal access, and increase overall system resistance to threats.
4. Regularly Review and Update Security Practices
Continuously monitor your ERP system for any possible risks and adjust security measures accordingly. Regular upgrades ensure that your protections stay effective in the face of evolving cybersecurity threats.
ERP Security Solutions with ScaleOcean
In today’s digital landscape, protecting your business data is more critical than ever. Cyber threats, data breaches, and compliance violations can lead to financial losses, operational disruptions, and reputational damage.
Without the right security measures, your ERP system becomes a prime target for cyberattacks. That’s why a proactive security strategy is essential to prevent breaches before they happen.
ScaleOcean offers tailored ERP security solutions designed to safeguard your organization from these risks, ensuring your system remains secure, resilient, and compliant. Experience firsthand how our solutions can strengthen your ERP security, request a free demo, and take the first step toward a safer, more protected business environment through our key services.
- Risk Assessment: Identifying potential vulnerabilities within your ERP system.
- Security Implementation: Deploying robust security measures to protect your data.
- Ongoing Support: Providing continuous monitoring and support to ensure sustained security.
- Regulatory Compliance: Ensures contracts and operations comply with laws, reducing legal risks.
- Access Control & Security: Manages user access to sensitive data, protecting confidentiality.
- Integration with Other Modules: Ensures consistent security across all integrated systems.
By choosing ScaleOcean, you help your team to focus on business growth and innovation while we handle system protection. Let’s build a safer, more secure digital future together. Get started today and take the first step toward stronger ERP security.
Conclusion
Protecting your ERP system is essential for business continuity and compliance. Cyber threats and data breaches can disrupt operations, leading to financial and reputational damage. Strong security measures, such as access controls, encryption, and continuous monitoring, help mitigate these risks, keeping your business secure and operational.
ScaleOcean’s ERP security solutions provide you with a trusted partner that is committed to protecting your system from developing risks. Our comprehensive solution includes risk assessments, advanced security installations, and continuing protection to keep your company compliant and resilient. A well-secured ERP system not only prevents cyber incidents but also provides your firm with trust, efficiency, and peace of mind.
FAQ:
1. What does ERP stand for?
ERP, or Enterprise Resource Planning, refers to a comprehensive system businesses use to gather, manage, and analyze data from essential functions such as finance, human resources, supply chain, and operations. It integrates different processes to improve efficiency and communication across departments.
2. What are the 4 types of security?
The four key types of security are physical security to protect tangible assets and personnel, cybersecurity to defend against digital threats, information security to maintain the confidentiality and integrity of data, and operational security to safeguard business operations from risks.
3. What are the 5 principles of security?
The five fundamental principles of security include Confidentiality (ensuring data privacy), Integrity (maintaining the accuracy of data), Availability (ensuring access to information), Authentication (verifying identities), and Non-repudiation (providing proof that actions were taken and cannot be denied).
4. What are the 5 P’s of security?
The 5 P’s of security include Plan (creating strategies), Protect (implementing protective measures), Prove (demonstrating compliance), Promote (raising awareness), and Partner (fostering collaboration among teams and stakeholders to enhance security efforts).







 PTE LTD..png)
.png)

.png)






.png)
.png)